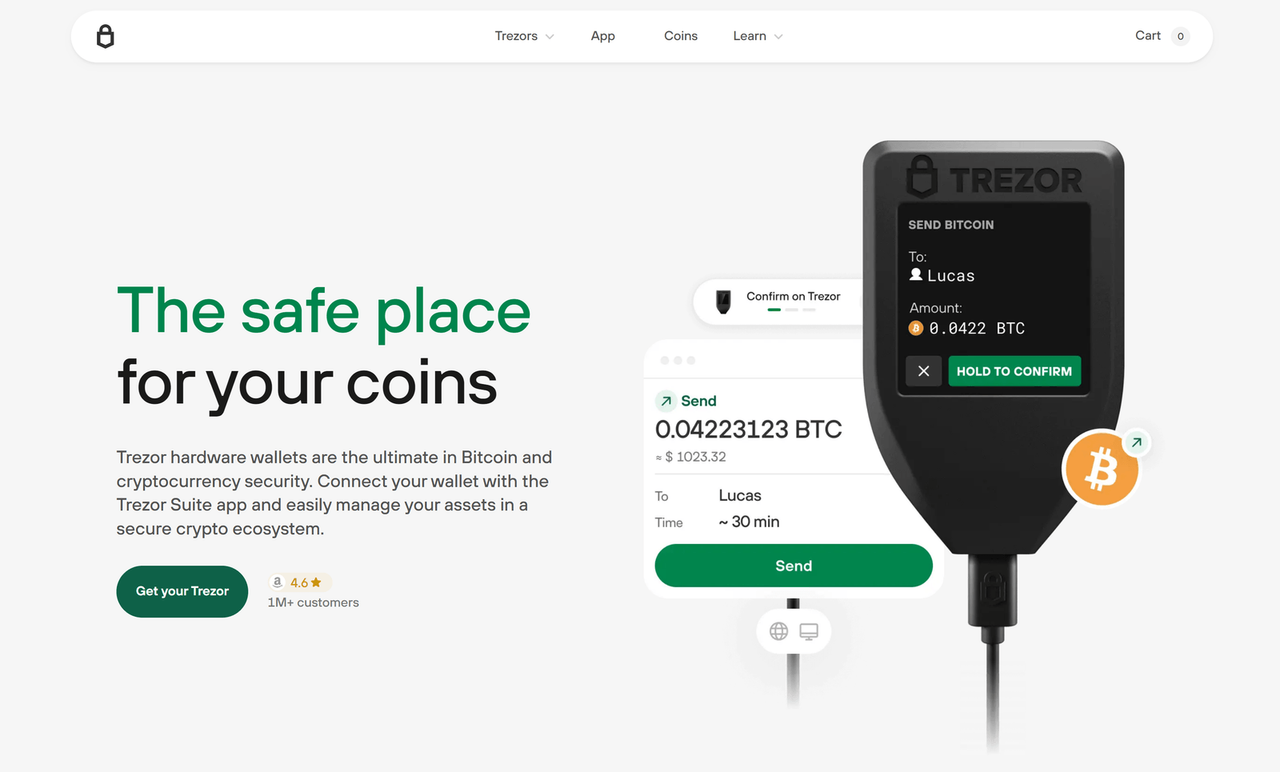
Trezor Bridge Guide | Secure Connection for Trezor
Trezor Bridge Guide | Secure Connection for Trezor provides a comprehensive overview of how to securely connect your Trezor hardware wallet to your computer or mobile device. This guide ensures safe communication with Trezor Suite® and supported browsers for seamless cryptocurrency management.
Trezor Bridge Guide | Secure Connection for Trezor: What It Is
Trezor Bridge Guide | Secure Connection for Trezor explains the role of Trezor Bridge in facilitating communication between your Trezor device and Trezor Suite®. It securely transmits transaction requests, confirmations, and wallet data, ensuring smooth and protected access to crypto assets.
Trezor Bridge Guide | Secure Connection for Trezor: Installation Steps
Follow these steps for Trezor Bridge Guide | Secure Connection for Trezor installation:
- Download the latest Trezor Bridge version from the official Trezor website.
- Run the installer and follow on-screen instructions to complete Trezor Bridge Guide | Secure Connection for Trezor installation.
- Reconnect your Trezor device to verify the secure connection during Trezor Bridge Guide | Secure Connection for Trezor.
- Open Trezor Suite® or your supported browser to confirm communication between your device and software for Trezor Bridge Guide | Secure Connection for Trezor.
Trezor Bridge Guide | Secure Connection for Trezor: Security Features
Trezor Bridge Guide | Secure Connection for Trezor ensures your crypto transactions and wallet interactions are secure. Features include:
- End-to-end encryption between your Trezor device and computer.
- Device verification to confirm only authorized hardware communicates with Trezor Suite®.
- Protection against phishing attacks while performing transactions with Trezor Bridge Guide | Secure Connection for Trezor.
Trezor Bridge Guide | Secure Connection for Trezor: Benefits
Using Trezor Bridge Guide | Secure Connection for Trezor provides:
- Reliable and smooth communication between Trezor hardware wallets and software.
- Quick transaction confirmations and real-time wallet updates.
- Compatibility with multiple browsers and operating systems for seamless crypto management with Trezor Bridge Guide | Secure Connection for Trezor.
Trezor Bridge Guide | Secure Connection for Trezor: Troubleshooting
If you encounter issues during Trezor Bridge Guide | Secure Connection for Trezor:
- Ensure your Trezor firmware is up to date.
- Reinstall Trezor Bridge from the official website.
- Restart your computer and reconnect your Trezor device to complete Trezor Bridge Guide | Secure Connection for Trezor.
Trezor Bridge Guide | Secure Connection for Trezor: Best Practices
Follow these best practices to maintain security and smooth operation during Trezor Bridge Guide | Secure Connection for Trezor:
- Only download Trezor Bridge from official sources.
- Keep Trezor Suite® and your device firmware updated.
- Avoid using public or unsecured networks when accessing your wallet through Trezor Bridge Guide | Secure Connection for Trezor.
Conclusion – Trezor Bridge Guide | Secure Connection for Trezor
In conclusion, Trezor Bridge Guide | Secure Connection for Trezor provides the essential tools and instructions to establish a secure connection between your Trezor hardware wallet and computer. By following installation steps, security practices, and troubleshooting tips, users can manage cryptocurrency safely and efficiently.
Disclaimer: The information in Trezor Bridge Guide | Secure Connection for Trezor is for educational purposes only. Cryptocurrency transactions carry risks. Always follow official Trezor guidance and secure your recovery seed, PIN, and device.